Attach the IAM role to your Workspace
If you are running this at an AWS hosted event (such as re:Invent, Kubecon, Immersion Day, Dev Day, etc), the IAM role has been created for you so the IAM role you are attaching in this step will be different, e.g. mod-*****, than if you were to create your own IAM role, e.g. tigera-workshop-admin.
-
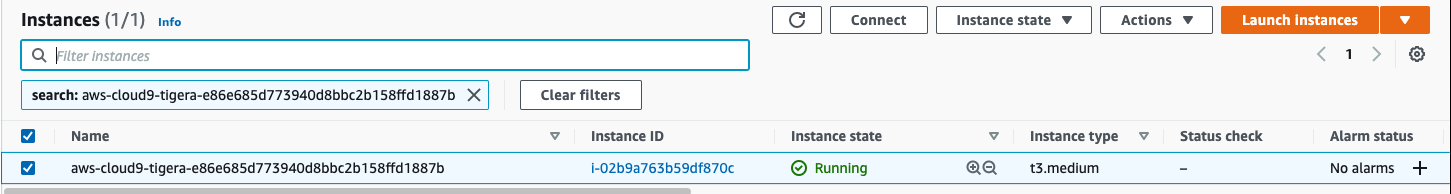
Follow this deep link to find your Cloud9 EC2 instance
Note: If no instances are found, click the gear icon in the top right corner and verify that “Use regular expression matching” is enabled. -
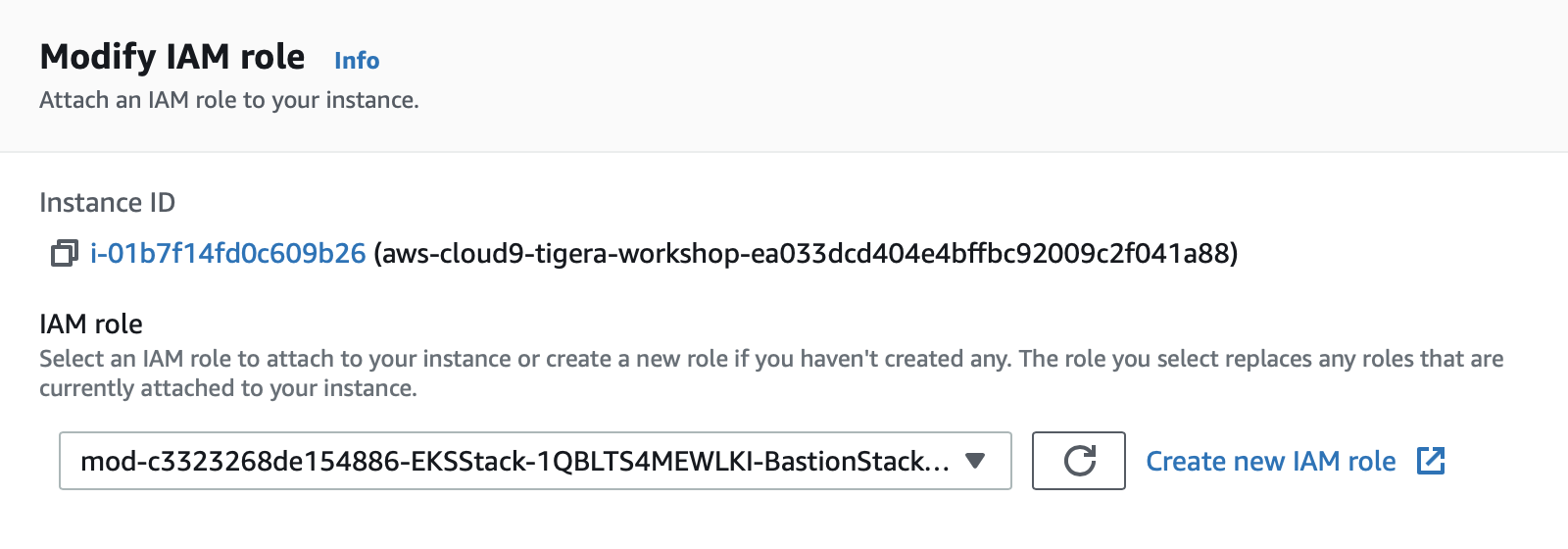
Select the instance, then choose Actions / Security / Modify IAM Role
-
Choose mod-c3323268de154886-EKSStack-1OVJRE9V-BastionRole-1FFSLTAUE5LK8 from the IAM Role drop down, and select Apply
At the AWS hosted event your IAM role name should start with mod- while in a self-paced workshop you can choose your own IAM role name. The default instructions for self-paced workshop use IAM role name tigera-workshop-admin.
-
Update IAM settings for your workspace.
Cloud9 normally manages IAM credentials dynamically. This isn’t currently compatible with some AWS services authentication, so we will disable it and rely on the IAM role instead.
-
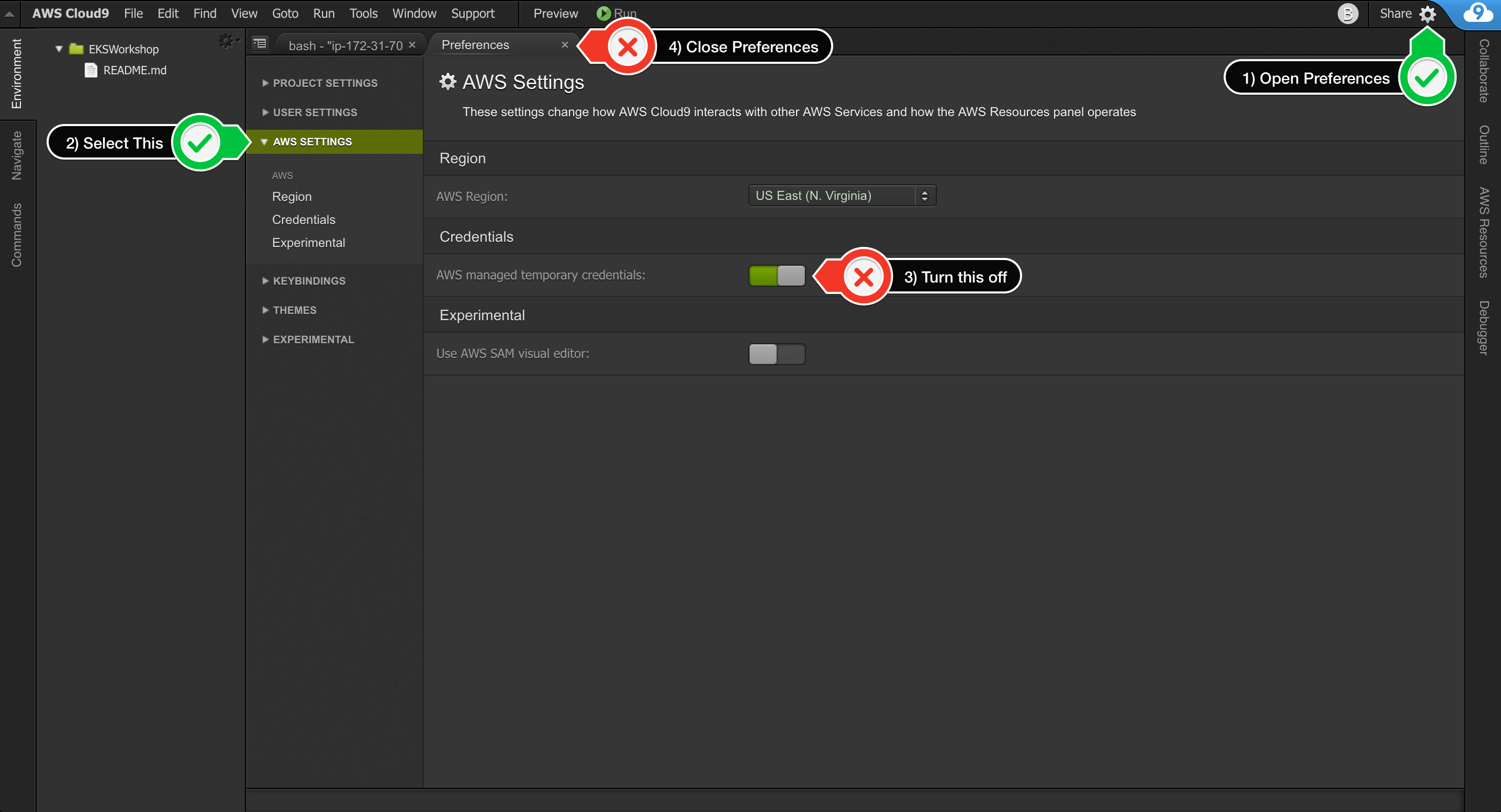
Return to your Cloud9 workspace and click the gear icon (in top right corner)
-
Select AWS SETTINGS
-
Turn off AWS managed temporary credentials
-
Close the Preferences tab
-