Module 3: Use security alerts and leverage dynamic packet capture
Estimated time: 20 min
Learning objectives
- Use global alerts to notify security and operations teams about unsanctioned or suspicious activity.
- Configure packet capture for specific pods to capture packet payload for further forensic analysis and explore the captured payload.
Use security alerts
We deployed security alerts in the first module. While we were implementing the use cases, some of them have triggered the alerts and now we can explore them.
Review alerts manifests.
Navigate to
demo/50-alertspath and review YAML manifests that represent alerts definitions. Each file containes an alert template and alert definition. Alerts templates can be used to quickly create an alert definition in the UI.View triggered alerts.
Open
Alertsview to see all triggered alerts in the cluster. Review the generated alerts.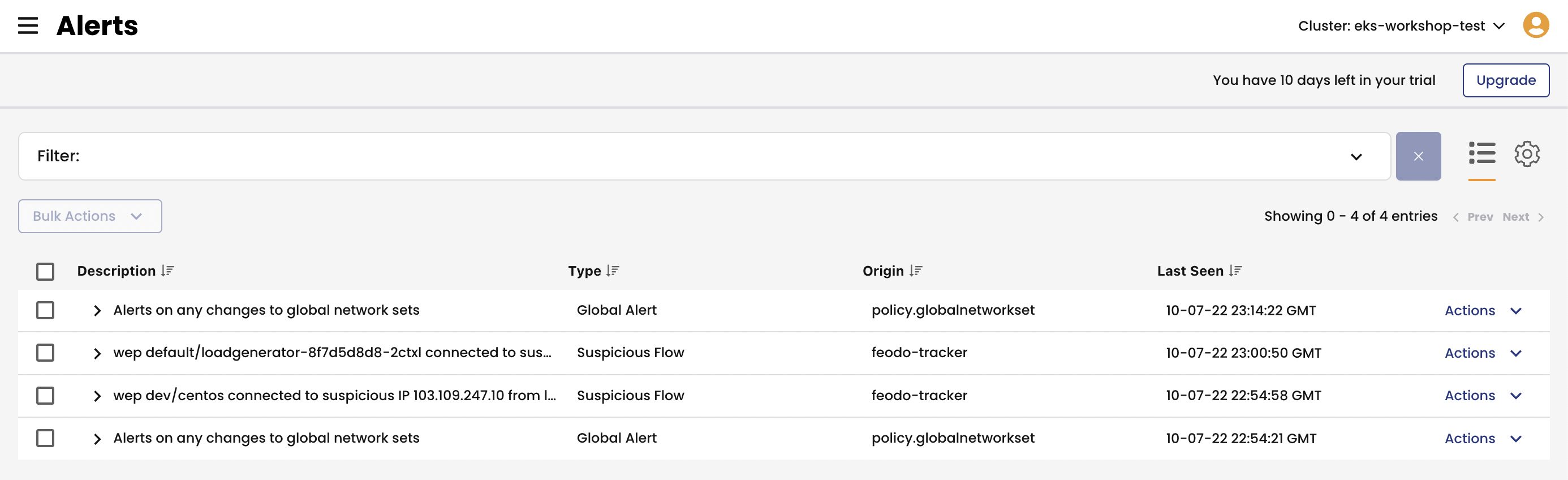
You can also review the alerts configuration and templates by navigating to alerts configuration in the top right corner.
Leverage dynamic packet capture
Refer to packet capture documentation for more details about this capability.
Configure packet capture.
Navigate to
demo/60-packet-captureand review YAML manifests that represent packet capture definition. Each packet capture is configured by deploing aPacketCaptureresource that targets endpoints usingselectorandlabels.Deploy packet capture definition to capture packets for
dev/nginxpods.kubectl apply -f demo/60-packet-capture/nginx-pcap.yamlOnce the
PacketCaptureresource is deployed, Calico starts capturing packets for all endpoints configured in theselectorfield.Install
calicoctlCLIThe easiest way to retrieve captured
*.pcapfiles is to use calicoctl CLI.CALICO_VERSION=$(kubectl get clusterinformation default -ojsonpath='{.spec.cnxVersion}') # download and configure calicoctl curl -o calicoctl -O -L https://docs.tigera.io/download/binaries/${CALICO_VERSION}/calicoctl chmod +x calicoctl sudo mv calicoctl /usr/local/bin/ calicoctl versionFetch and review captured payload.
The captured
*.pcapfiles are stored on the hosts where pods are running at the time thePacketCaptureresource is active.Retrieve captured
*.pcapfiles and review the content.# get pcap files calicoctl captured-packets copy nginx-pcap --namespace dev ls dev-nginx* # view *.pcap content tcpdump -Ar $(ls dev-* | head -1) tcpdump -Xr $(ls dev-* | head -1)Clean up packet capture resource
If a packet capture resource does not have
endTimefield, the capture would be continuous until the resource is removed.Stop packet capture by removing the
PacketCaptureresource.kubectl delete -f demo/60-packet-capture/nginx-pcap.yaml
Note Packet Captures can also be created and scheduled directly from the Calico UI. Follow the Service Graph method for this alternative procedure.
Configure deep packet inspection for sensitive workloads
Refer to deep packet inspection documentation for more details about this capability.
Configure deep packet inspection (DPI) resource.
Deploy DPI resource to allow Calico inspect packets bound for
dev/nginxpods.kubectl apply -f demo/70-deep-packet-inspection/nginx-dpi.yamlOnce the
DeepPacketInspectionresource is deployed, Calico configures DPI controller to scan packets for endpoints matching theselectorfield configuration.Wait until all DPI pods become
Readywatch kubectl get po -n tigera-dpiSimulate malicious request and review alerts.
Query
dev/nginxapplication with payload that triggers a Snort rule alert.kubectl -n dev exec -t centos -- sh -c "curl http://nginx-svc/secid_canceltoken.cgi -H 'X-CMD: Test' -H 'X-KEY: Test' -XPOST"Navigate to the Alerts view in Tigera UI and review alerts triggered by DPI controller. Calico DPI controller uses Snort signatures to perform DPI checks.